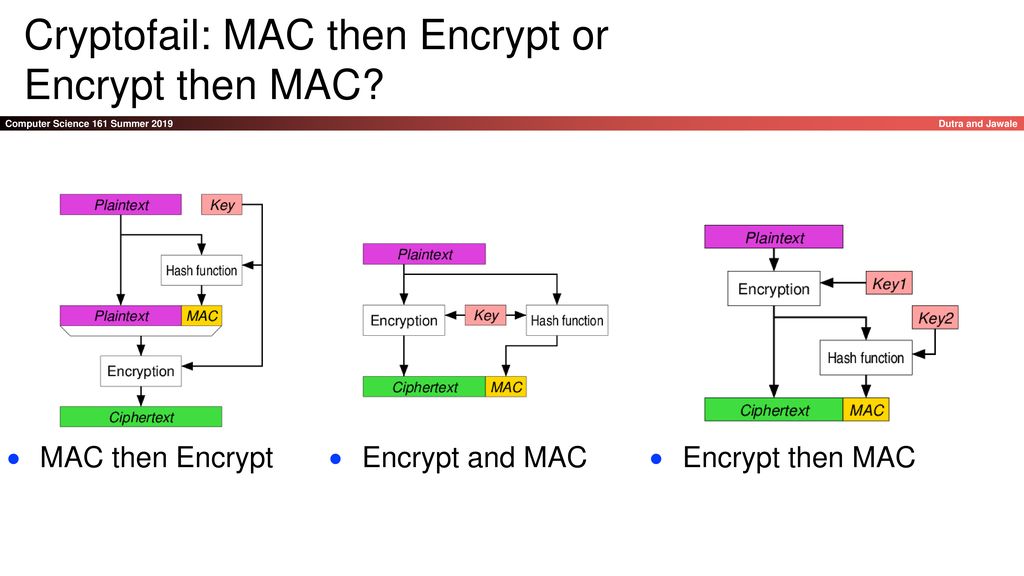
hmac - Why do we encrypt then decrypt then encrypt data with different keys? - Cryptography Stack Exchange
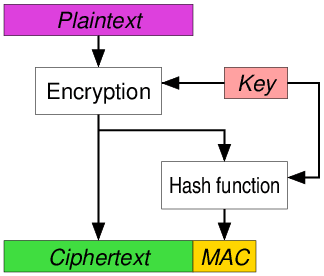
Magnus K Karlsson: Symmetric Authenticated Encryption (AE) or Authenticated Encryption with Associated Data (AEAD)
GitHub - lpoulain/break_MAC-then-encrypt: Cryptography: a proof-of-concept attack against the MAC-then-encrypt scheme
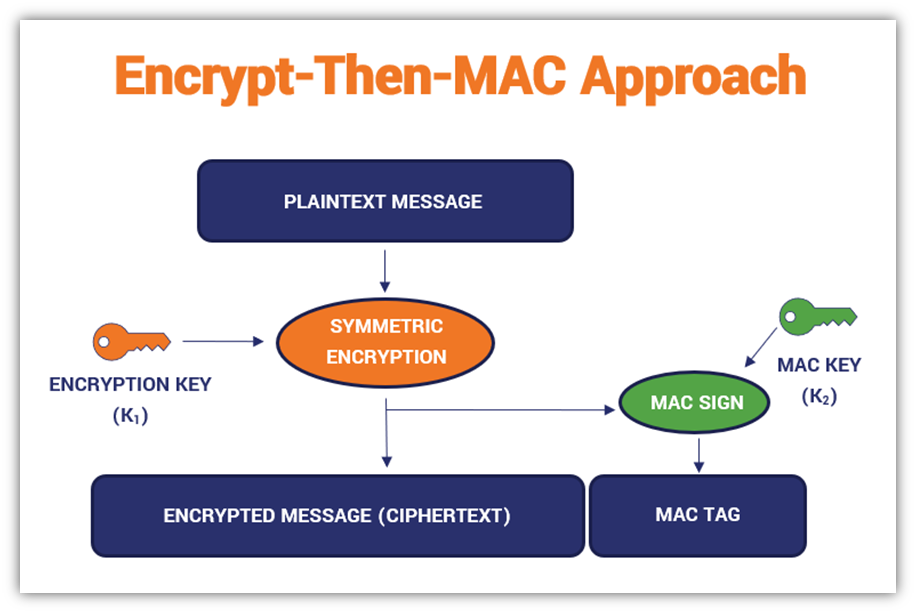
GitHub - SoursosK/Encrypt-then-MAC: A demo app applying the Encrypt-then-MAC scheme to a phrase, using AES-CBC 256 and HmacSHA256.
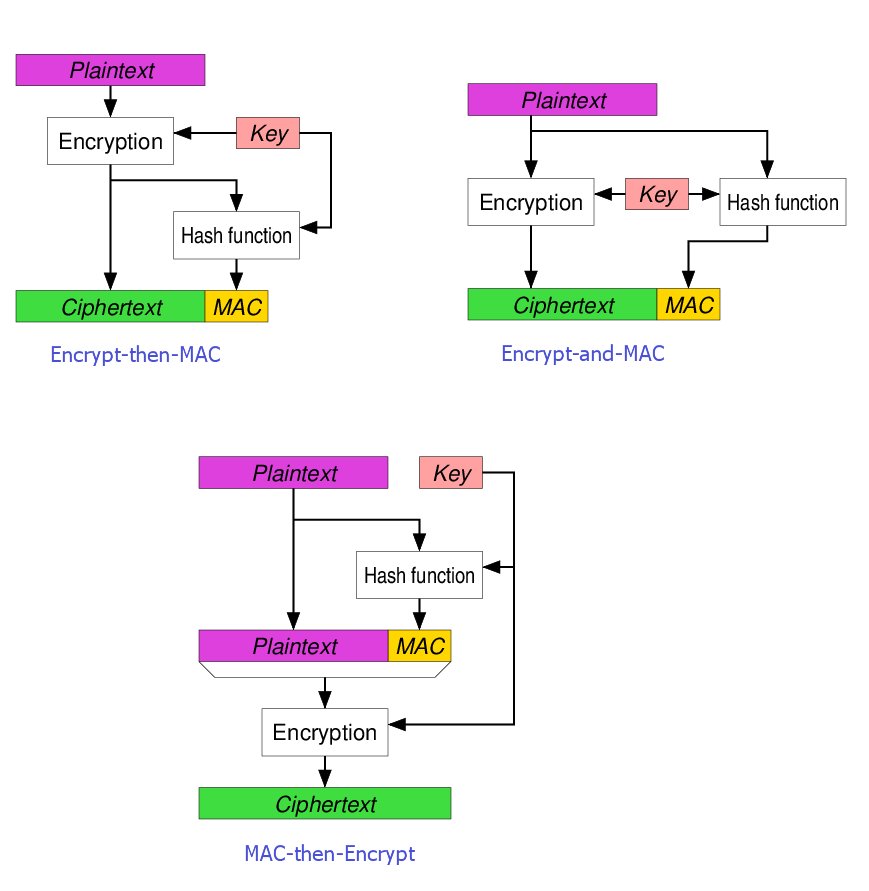
GK Palem on Twitter: "Among the three methods for #Blockchain #Ciphers the Encrypt-Then-MAC has been regarded as the highest definition of security with "strongly unforgeable" MAC, compared with MAC-then-encrypt or Encrypt -and-MAC. Authenticated